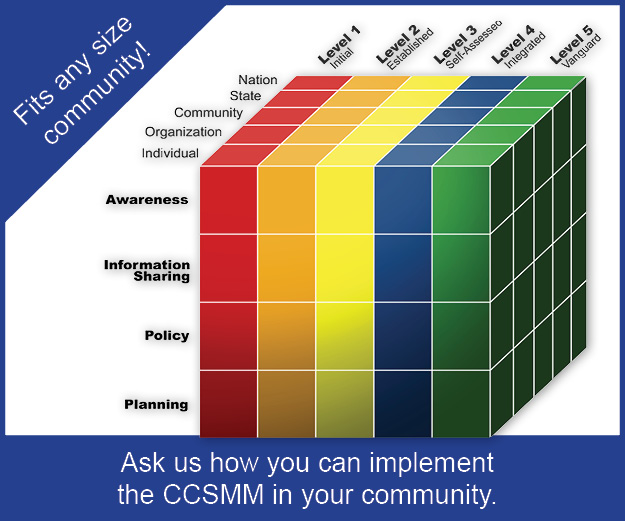
Establishing or enhancing your cybersecurity program can feel a little overwhelming at times. There are many areas that you may want to address and prioritizing which comes first isn’t always as easy as it appears. The best way to approach this is to have a plan in place that first assists you in recognizing what is already in place and then provides a roadmap on how you will build and enhance the program. Your program should include four areas of improvement. Those four areas should be cybersecurity awareness, information sharing, policies and plans.
Awareness
Most people understand that cyber threats exist, however not as many understand the extent of the threat, the current attack trends, how a cyber incident can impact an organization or community, what the vulnerabilities are that should be addressed, and what the cascading effects may be if under a cyber-attack.
Information Sharing
There is often confusion, conflicting opinions or it is unknown what someone should do with information on a cyber incident and where the information should be reported. Information sharing should be used to address what organizations should do with cyber-related information both internally and externally. If an organization is willing to share certain types of cyber-related information, who specifically will they share it with both inside and outside of their organization, and in what time frame should they share it? A related, and equally important, question is how the information will be shared.
Policy
Cybersecurity principles need to have cybersecurity included in them. Policies that are not cybersecurity specific may not be executed consistently and may not be interpreted the same way throughout the organization or community. Policies need to have cyber elements integrated into them. This includes all guiding regulations, laws, rules and documents that govern the daily operation of the organization or the community.
Plans
Continuity, incident response, emergency and disaster recovery plans need to include cybersecurity principles. Plans will address how to prepare, mitigate, respond to and recover from cyber incidents. They need to identify how cyber can impact the organization or whole community and need to include the cascading effects a cyber incident may cause. Each plan should be analyzed to identify cyber resources and actions needed and include them in the overall strategy to achieve objectives.
When establishing or enhancing your cybersecurity program, first evaluate where you are at in terms of the maturity in each of these areas. Next you will want to decide what level of maturity you believe your organization or community needs to be to address the cyber threat. There are five levels you may want to consider. Each level is briefly described below:
Initial Level
Everyone starts at the Initial level, which is where you start planning for your cybersecurity program. At this level, there may not be processes that are needed for cybersecurity and there may not be a cybersecurity program. The Initial level takes into consideration there may be no budget or a minimal budget to add cybersecurity initiatives into your program. Therefore, efforts are limited, as much as possible, to no- and low-cost items to help get started.
Established
The Established level is when a basic program is in place and has elements of awareness, information sharing, policies and plans. The cybersecurity awareness program includes some cybersecurity training and there is at least informal information sharing occurring. Policies and plans may not have cybersecurity integrated completely but the need to integrate cybersecurity into policies and plans is recognized.
Self-Assessed
At this level, there is an awareness of cybersecurity gaps in the current security posture. Establishing baselines is occurring or is completed. Information sharing is happening on a regular basis and processes and procedures are being refined. Each of these areas is being monitored and measured for effectiveness. Cyber incident response and recovery is formalized at this level. Organizations should be able to, and should actually be conducting efforts, to help each other improve their cybersecurity postures.
Integrated
Cybersecurity at this level is no longer a separate component to the operations but recognize that cybersecurity is cross-cutting and impacts every aspect of the organization or community. Thus, cybersecurity needs to be considered by everyone and everyone’s role in cybersecurity has been communicated. Exercises should be focused on blended attacks that affect both physical and cyber assets or functions. The integrated level incorporates efforts with all members and organizations within the community as well as working with the state and other communities.
Vanguard
The Vanguard level means your cybersecurity posture is fully-vigilant. Cybersecurity programs include the entire population of the community. Exercises are full-scale events and are as realistic as possible. Information sharing is at its most advanced state where fusion and dissemination of data received from various sources occurs at an acceptable pace and is as close to real-time as possible. Mentorship programs increase cybersecurity and information sharing capabilities of others. The program is routinely evaluated to maintain and ensure capabilities continue to meet your needs.
Not all organizations or communities have to be at the same level and do not need to attain the highest level.
Connect with the CIAS-ISAO to learn more about establishing your Cybersecurity Program and determining what level you should achieve by emailing cias@utsa.edu.