by Natalie Sjelin, Assoc. Director of Training, CIAS-ISAO
Information sharing is a key element of any cybersecurity program. It is essential in the protection and detection aspects of programs such as the NIST Cybersecurity Framework. And information sharing helps to alert other organizations to ongoing reconnaissance and attack efforts by attackers. The information sharing community has learned that, when it comes to cybersecurity, organizations are not in competition with each other but instead are partners in a mutual defense against attackers. This has not been an easy lesson to learn. It has taken time but today there are many robust information sharing programs that help various sectors and geographic regions to band together to help thwart attacks against any member of the group.
Information sharing is used to address what organizations should do with cyber-related information both internally and externally. If an organization is willing to share certain types of cyber-related information, who will they share it with both inside and outside of their organization, and in what time frame should they share it? A related, and equally important, question is how the information will be shared. As an organization or community matures in their security processes, their information sharing processes will change significantly.
The dynamic of sharing information about cyber incidents or attacks is a difficult one. There is a hesitancy to share cyber-related information because there is a fear that sharing information might harm the organization. With this in mind, how do organizations overcome these challenges? If everyone shared all information regarding their cyber infrastructures, would this generate information overload where organizations have more information than can be effectively managed? How will organizations separate the actionable, meaningful information from the disparate and fragmented information that may not be useful in the current context?
Information sharing is not something that organizations are immediately comfortable with doing. This is especially true for information related to compromises of security, where information could possibly be used for a competitive advantage. For an organization to be comfortable with sharing this type of information it must trust that those organizations will not use information that’s shared in a way that would be detrimental to them. One of the best ways to establish trust is through personal contact and working together.
There are two important points related to information sharing. The first is that an organization only has to share information that it is willing to share. It does not need to include information that the organization is not comfortable sharing. While organizations need to comply with laws, such as breach notification laws, the type of information being shared in the community program is separate from the information that may be required because of a law or regulation.
The second point is that the programs that are flourishing are doing so because the members have realized that when it comes to security, the “contest” is not between competing companies in a given sector; instead, it is between all members of the sector and the cyber-attackers. The members of the sector are on one side and the individuals attempting to compromise the systems of one or more members of that sector are on the other side. When organizations realize that they are on the same side and that it behooves them to share, and to not abuse information that has been shared with them, then two-way information sharing is more likely to occur.
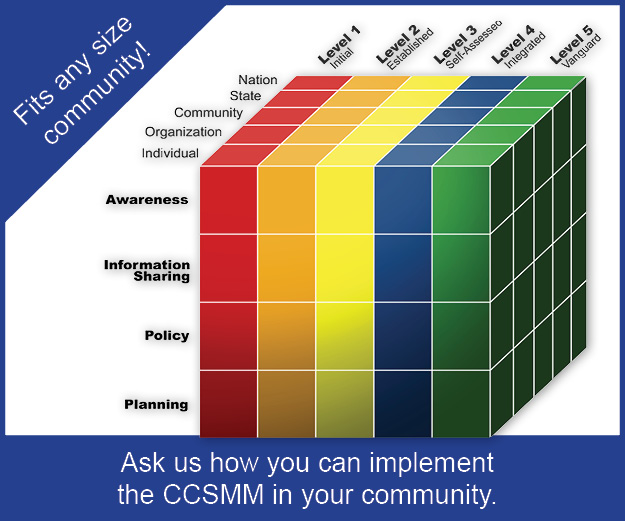
There are roles for information sharing at the individual, organization, community, state and national levels. For our purposes, this article will introduce sharing at the individual, organizational and community levels:
Individual Information Sharing
The individual includes everyone who uses technology in some form. Improving an individual’s cybersecurity preparedness begins with the internet connected devices they use personally and are responsible for securing themselves, such as smartphones and home wireless technologies. It should also include their online computing habits.
Information sharing programs should recommend that individuals know who to report suspicious or malicious activities to, when and how to report them.
Organizational Information Sharing
The areas covered by the organization scope includes small businesses, government agencies, non-profit organizations, mid-size companies and large corporations. Essentially, the organization is any business activity in a community. An organization’s cybersecurity preparedness should include the individuals or employees, its customers, partners and supply chain. Its preparedness capabilities should also include the organizations assets including information, computers and networks.
Organizations should consider information sharing both inside their organization and outside. Employees should know who within the organization to report suspicious activity to. They should also address how to escalate cyber incident information to levels of management for their situational awareness and in more critical situations, to make decisions for the business.
It should also be determined what types of cyber incidents will be reported outside the organization, to whom and what threshold must be reached to trigger external reporting. It’s a good practice to consult legal counsel to ensure compliance, privacy and other regulatory requirements have been considered. Establishing relationships and building trust with organizations and agencies before an incident will make the whole process easier because it is already known who to contact, what to expect and what to ask for.
Initial Information Sharing Policies any organization should include:
- Reporting incidents to law enforcement
- Receiving cyber threat intelligence
- Sharing information internally before, during and after an incident
- Sharing information externally
- Legal Purposes (compliance)
- Cooperative Security purposes
- Sharing with the government (an organization should consider if they wish to share with the government and their policies should reflect this)
These are the initial areas to address when creating an information sharing program. There will be a multitude of other policies that you may want to incorporate as your program matures. If your organization already has an information sharing program, these policies should already exist. If they do, review them and ensure they cover the sharing capability adequately. If they do not exist, these are policies that can start your program.
Community Information Sharing
The community scope is a defined geographical area that includes small, mid-size and large businesses, local government, emergency services, non-profit organizations, critical infrastructure, and the citizens living in that geographical area. The community will determine the area covered by the community scope that will be included in their cybersecurity preparedness; for example, a community may determine their cybersecurity program will include the surrounding cities and counties that are on the outskirts of the metropolitan area. Alternatively, the smaller cities or counties will have their own cybersecurity program but may look to the larger community as a mentor.
Communities will need to consider information sharing both inside their community and outside, and will need to understand what cyber threat indicators are needed to recognize the community is under a cyber-attack.
Communities need to address how to escalate cyber incident information to state and national agencies. In addition, the types of cyber incidents that will be reported outside the community needs to be determined, who it should be reported to, and what threshold must be reached to trigger that reporting. Building relationships and establishing trust with these organizations and agencies before an incident will assist to ensure the information shared is timely, relevant and actionable.
Recommendations around community information sharing of a cyber incident include the following:
- Develop a coordinated community information-sharing initiative or working group, utilizing already established programs and organizations wherever possible, to examine interdependencies and develop or improve information sharing processes
- Create contact lists to use in the event that a cyber incident occurs, and update them regularly
- Identify local cybersecurity experts and create a cyber incident response team for the community. Encourage organizations within the community to establish their own, if they haven’t already
- Consider cooperative recurrent training programs across the community to establish relationships across sectors while also providing new and updated information throughout the community
- Establish clear thresholds for when and how to share information about cybersecurity incidents based on what is normal for the organization or community
- Develop processes to accomplish bidirectional information sharing that effectively accommodate receiving information as well as transmitting it, and ensure that these processes take into account external reporting requirements and laws
- Expand connections to neighboring communities to facilitate information sharing
- Coordinate breakfasts, luncheons and/or conferences for community members with discussion topics related to cybersecurity
- Encourage community members to join, and, if they don’t already exist, establish local chapters of security organizations such as ISSA, ISACA, ASIS and InfraGard
- Community organizations should determine the value of information used by their organization and prioritize that information based on that analysis.
Information sharing is a key element that should be included in your cybersecurity program. If you are interested in more detailed information about establishing a community cybersecurity program, contact the CIAS-ISAO team.