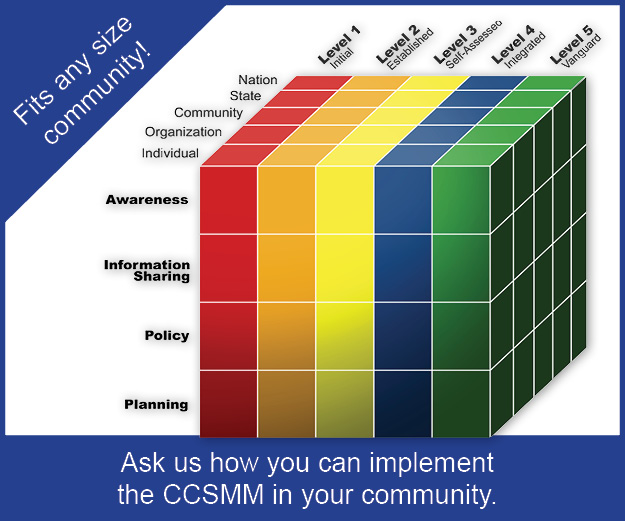
The Crucial Function of Cybersecurity Policies in Organizations
The importance of cybersecurity cannot be emphasized enough in today’s connected society. Digital technology is at the core of every part of our lives; therefore, organizations must construct their defenses against cyber-attacks using cybersecurity policies as the framework. In this post, we will go into what typically makes up a security policy, as well as how to distinguish between control objectives, standards, guidelines and procedures. We will also look at why cybersecurity policies are so essential.