The importance of cybersecurity cannot be emphasized enough in today’s connected society. Digital technology is at the core of every part of our lives; therefore, organizations must construct their defenses against cyber-attacks using cybersecurity policies as the framework. In this post, we will go into what typically makes up a security policy, as well as how to distinguish between control objectives, standards, guidelines and procedures. We will also look at why cybersecurity policies are so essential.
To help you get started in developing your community’s cybersecurity program, the CIAS-ISAO has four initial, critical steps to guide you. Each step includes specific ways to help you accomplish them.
The MITRE ATT&CK framework is one of today’s most significant and publicly available cybersecurity knowledge bases. Organizations, cybersecurity analysts and practitioners should use MITRE ATT&CK because it fosters greater awareness of the security posture by gaps in defenses. More importantly, the ATT&CK lists methods to mitigate or interrupt attacker attempts to perform the specific technique. Moreover, the framework is designed to be used at all levels of the organization, from analysts to leaders. This article highlights the framework’s tactics with examples of how to share information within your organization.
The cultural icon Smokey Bear, with his yellow hat and wildfire prevention tagline, has been familiar to Americans for decades. Likewise, McGruff the Crime Dog, who encouraged the public to “Take a bite out of crime.” These famous characters has helped encourage a culture of security. But what about a culture of cybersecurity?
Since cybersecurity is a shared responsibility, the UTSA Center for Infrastructure Assurance and Security (CIAS) has launched Alan CyBear™, a new mascot to promote a more secure nation through cybersecurity awareness, prevention and defensive efforts.
A good defense requires that IT security professionals think like an attacker to defend their organizations tactically and preemptively. In general, security professionals need to develop “oblique thinking,” enabling an adversarial mindset that focuses on identifying assumptions and determining if and how these assumptions can be violated. This article focuses focus on the (1) reconnaissance, (2) scanning (3) and gaining access phases of hacking and how to defend against them.
Over the years, the security industry has been encouraging the highest levels of leadership to become more involved and knowledgeable in cybersecurity. Organizational leaders that need to be aware of cybersecurity are at all levels. Leaders can be the CEO, the board of directors, the school superintendent, a department head or a team lead. These leaders do not focus on the cybersecurity day-to-day details, but they do have unique roles in helping their organizations manage cybersecurity threats. Now is a great time to work with the leaders in your organization to be more cyber-knowledgeable and cyber-prepared.
Incident response addresses the question: “How well did you prepare?” Your response to that question is directly related to your preparation. This supports the adage that an ounce of prevention is worth a pound of cure—or response. This article takes a look at five basic lessons to consider when mitigating incidents to help you prepare and prevent a potential cyber incident.
Incident Response Plans are critical to an organization's ability to minimize damage caused by threats, including data loss, abuse of...
A community with an established cybersecurity program and established information sharing processes will be much more likely to be able to effectively respond to cyber events impacting them. This article introduces the topic of whole-community cybersecurity programs and five key reasons why they are needed.
Register for a one-hour webinar on October 26th with the CIAS-ISAO Associate Director of Technology and Research Dwayne Williams, as he provides insights into no-cost tools that can help you monitor and secure your organization’s IT infrastructure.
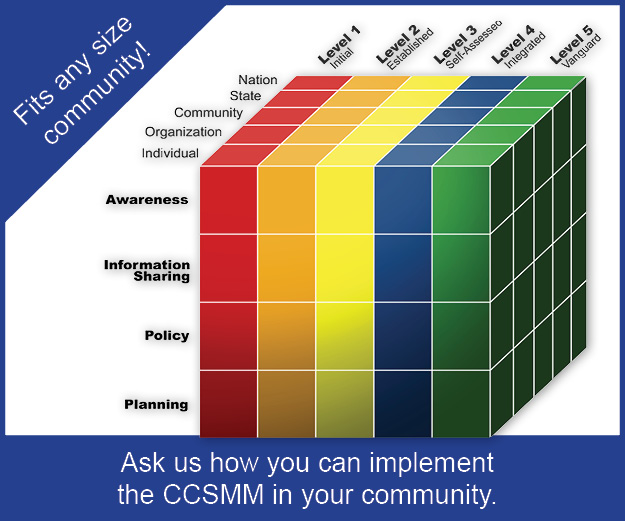
The CIAS-ISAO was established to help states, local jurisdictions, tribes and territories (SLTTs) to establish comprehensive cybersecurity programs by using the Community Cyber Security Maturity Model (CCSMM). This multi-dimensional model provides a roadmap and common point of reference for organizations looking to create viable and sustainable cybersecurity programs.
Since 2004, members of the National Cybersecurity Preparedness Consortium (NCPC) have been working with the Department of Homeland Security (DHS) to provide research-based, cybersecurity training, exercises and technical assistance to local jurisdictions, counties, states and the private sector. These resources are available at no cost to participants! Learn more about these resources here!
In today’s increasingly connected world, it is more important than ever to ensure an organization’s information and information systems are protected from cyber threats. Every organization has critical information and technology assets that are essential and require enhanced security. However, due to finite organizational resources, a deliberate and strategically-focused approach is needed to identify – and secure – the most important assets. Gain a better understand of why formally identifying your high value assets – and mission essential functions – are critical to supporting your organization’s ability to conduct business.
The Center for Infrastructure Assurance and Security (CIAS) at The University of Texas at San Antonio has frequently used disinformation and misinformation in its community cybersecurity exercises to impact the ability of first responders to accomplish their mission. Consequently, it is our recommendation that communities need to be prepared to counter disinformation attacks that may occur in the community.
When it comes to cybersecurity, it is common to hear statements that you can’t protect against all attacks and be absolutely secure. Because of this, the goal of organizations should not be to try and make their computer systems and networks absolutely secure but rather they should concentrate on managing the risk to the organization. One necessary factor in risk management is an understanding of your IT environment including what systems and software you utilize.
The National Centers of Academic Excellence in Cybersecurity, as part of the National Security Agency (NSA), has awarded a grant in the amount of $1.67 million to the CIAS to help communities become more cyber secure nationwide. The CIAS will work with multiple communities during the two-year grant, beginning with Angelo State University and the city of San Angelo.
As a member, your ticket to the upcoming Webinar “Continuity Planning” is FREE. Just go here to register.
Register for a one-hour webinar on October 26th with the CIAS-ISAO Associate Director of Technology and Research Dwayne Williams, as he provides insights into no-cost tools that can help you monitor and secure your organization’s IT infrastructure.
Cyberattacks are occurring at the state and local level, impacting government, small businesses, academia and industry sectors, which ultimately impacts the individuals throughout the community. A whole-community approach needs to be taken by communities to protect their citizens. This begins at the K-12 level, helping educators access the tools and resources they need to create better cyber-aware citizens and support a growing cybersecurity workforce.
We know our infrastructures are targets for cyberattacks, both for cyber criminals as well as nation-states. Understanding the types of cyber attacks on critical infrastructure provides lessons on how to defend and protect against such attacks. This article also provides 11 steps that communities can take to prepare for an attack on one or more of their critical infrastructures.